Welcome to The Insider Threat. An OSINT CTF to gather intelligence on a missing person that carried out a cyberattack on the organisation they were working at.
This CTF has been provided by bushidotoken.net and is based on real life investigations.
The back story is that we have been tasked by a client whose network has been compromised and taken offline. Incident responders and digital forensic investigators are currently on the scene and have conducted a preliminary investigation. Their findings show how the attack was orchestrated from one user account at the company, meaning this was an insider threat.
The client has alerted the authorities, which are currently too busy to help at this time. The client has come to us asking for help to find the malicious employee who has since disappeared.
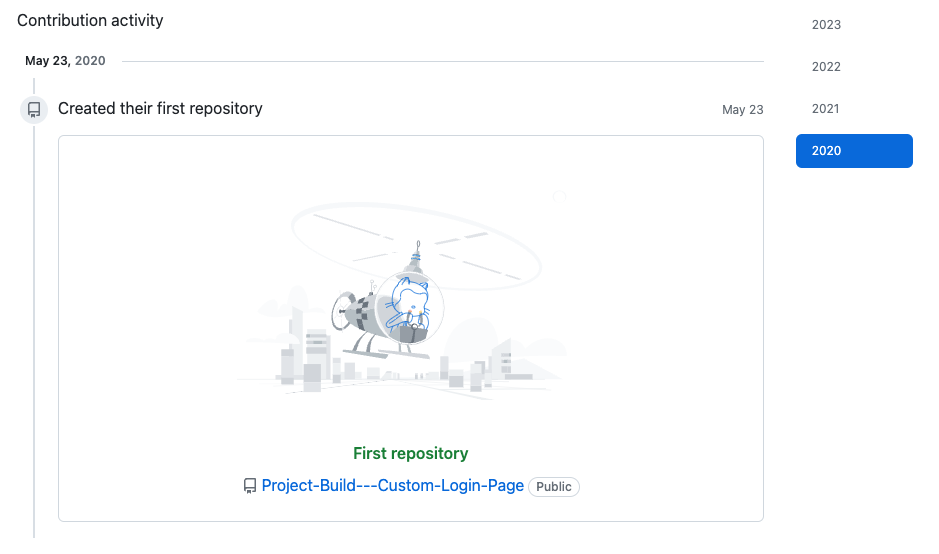
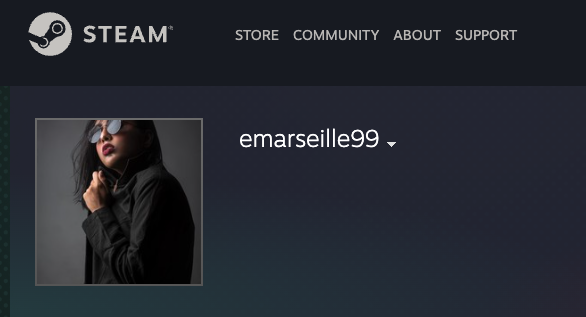
As a starting point we have been supplied with the employees GitHub account https://github.com/EMarseille99 and need to find out as much as we can from this information.
Task 1
Find out more information about the person of interests GitHub account.
[Question?] What is their API key?
This one’s pretty simple. Connecting to, and reading through some of the early code that user EMarseille99 has committed to their GitHub will provide us with this answer.
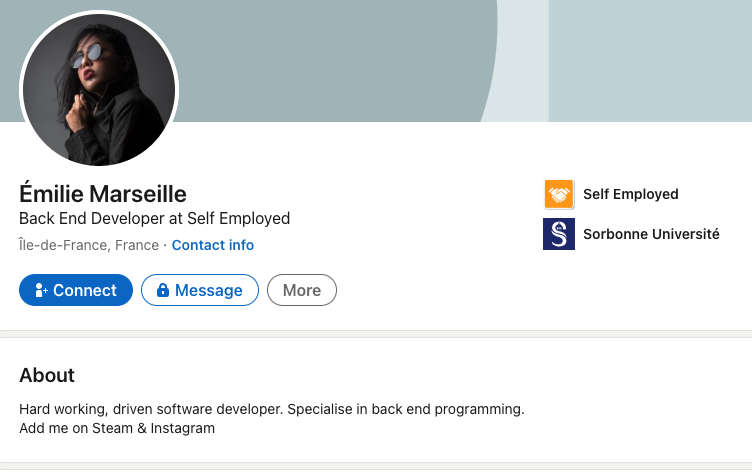
[Question?] What is their real name, job role, company and university?
A quick glance over the users GitHub profile shows a company name and a generic location of EU (European Union). I did some initial searching on Linkedin as this is the type of information provided there, but I had issues filtering my requirements by location and company name to get actionable results.
In the end I still focused on Linkedin, but this time carried out my search filtering direct through Google Dorks.
[Question?] What is their username and plaintext password?
Again, by reviewing the code in Login Page.js we can abstract useful information to answer this question.
Task 2
Looking at their GitHub account, what hacking tools did the person of interest use on company PCs?
Before starting this question, it’s good to just review and get familiar with the repositories and tools that Emilie has forked. While these aren’t proof that these tools were used by her as part of the incident being investigated, we can make assumptions that each of these tools served a purposed in part of this fictitious CTF.
(Some of) The Tools:
QuasarRAT
Quasar is a fast and light-weight remote administration tool (RAT) coded in C#. Quasar can be used to access Task Manager, Registry Editor, manage files and startup items, download/upload and execute files, access system information, run various computer commands, log keystrokes, steal passwords and access files stored on the computer.
Empire
Empire 3 is a post-exploitation framework that includes a pure-PowerShell 2.0 Windows agent, and compatibility with Python 3.x Linux/OS X agents. It is the merger of the previous PowerShell Empire and Python EmPyre projects. The framework offers cryptologically-secure communications and flexible architecture. Basically, Empire is a tool that is similar to Metasploit but specific to PowerShell. It allows you to run PowerShell scripts in memory and make a connection back to your machine.
Read more at https://www.bc-security.org/blog
Metasploit-framework
The Metasploit Framework is a Ruby-based, modular penetration testing platform that enables you to write, test, and execute exploit code. The Metasploit Framework contains a suite of tools that you can use to test security vulnerabilities, enumerate networks, execute attacks, and evade detection.
Read more at https://docs.rapid7.com
Meterpeter
Meterpreter is a Metasploit attack payload that provides an interactive shell to the attacker from which to explore the target machine and execute code. Meterpreter is deployed using in-memory DLL injection. As a result, Meterpreter resides entirely in memory and writes nothing to disk.
Mimikatz
Mimikatz is a tool made by gentilkiwi that is commonly used by hackers and security professionals to extract sensitive information, such as passwords and credentials, from a system’s memory.
Read more at http://blog.gentilkiwi.com/mimikatz
Hashcat
hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 300 highly-optimized hashing algorithms. hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and macOS, and has facilities to help enable distributed password cracking.
Read more at https://hashcat.net/wiki/
Bloodhound
BloodHound is an Active Directory reconnaissance and attack path management tool that uses graph theory to identify hidden relationships, user permissions, sessions and attack paths in a source Windows domain.
Read more at https://bloodhound.readthedocs.io
Nmap
Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection.
Read more at https://nmap.org
xmrig
XMRig High performance, open source, cross platform RandomX, CryptoNight, AstroBWT and Argon2 CPU/GPU miner, with official support for Windows.
[Question?] What was used for lateral movement and privilege escalation?
[Question?] What was used for remote control?
[Question?] What was used for reconnaissance?
[Question?] What was used for cryptocurrency mining?
[Question?] What was used for password cracking?
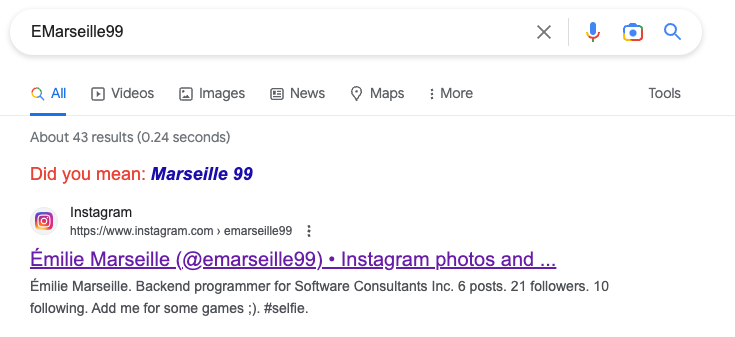
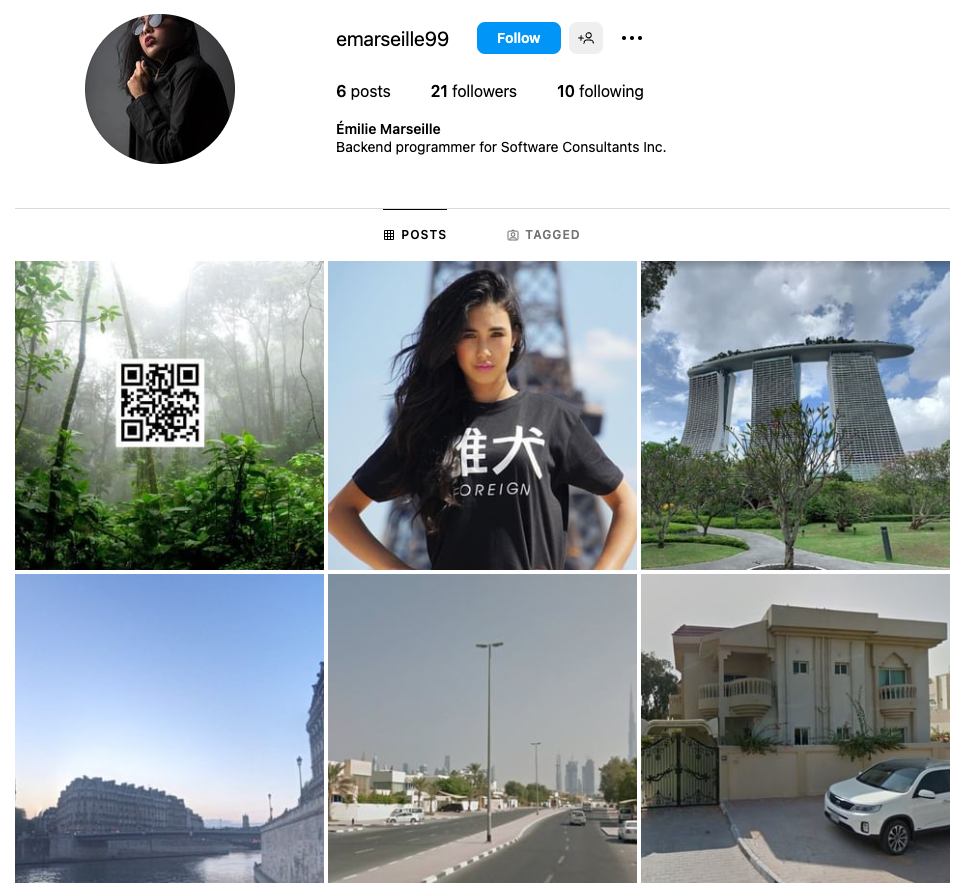
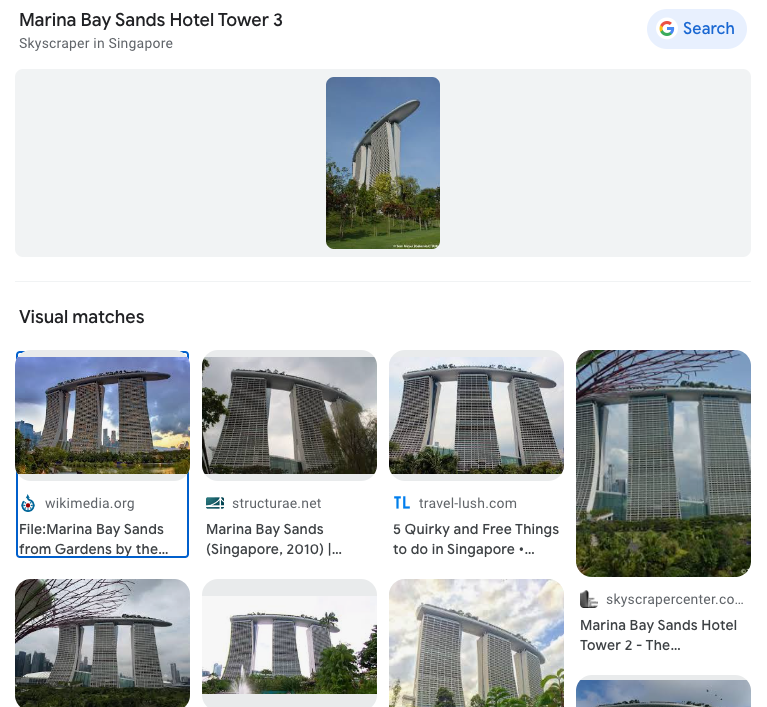
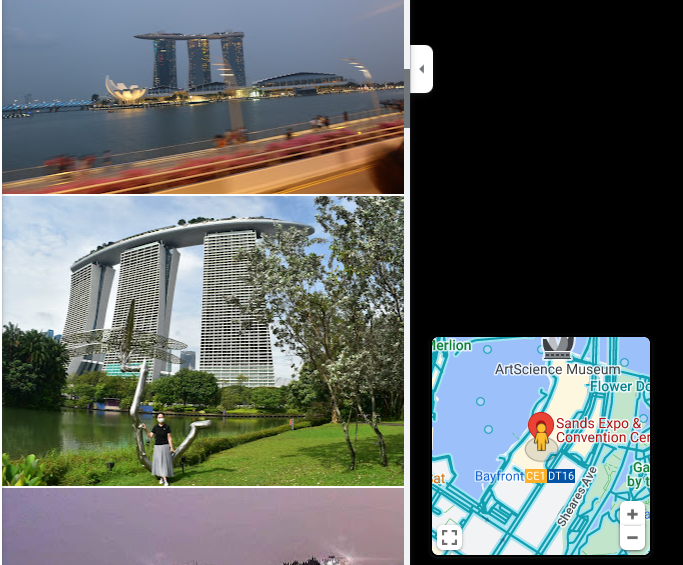
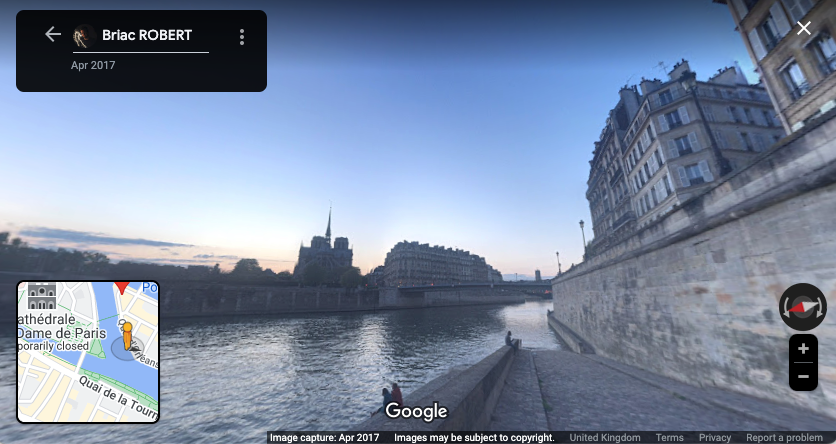
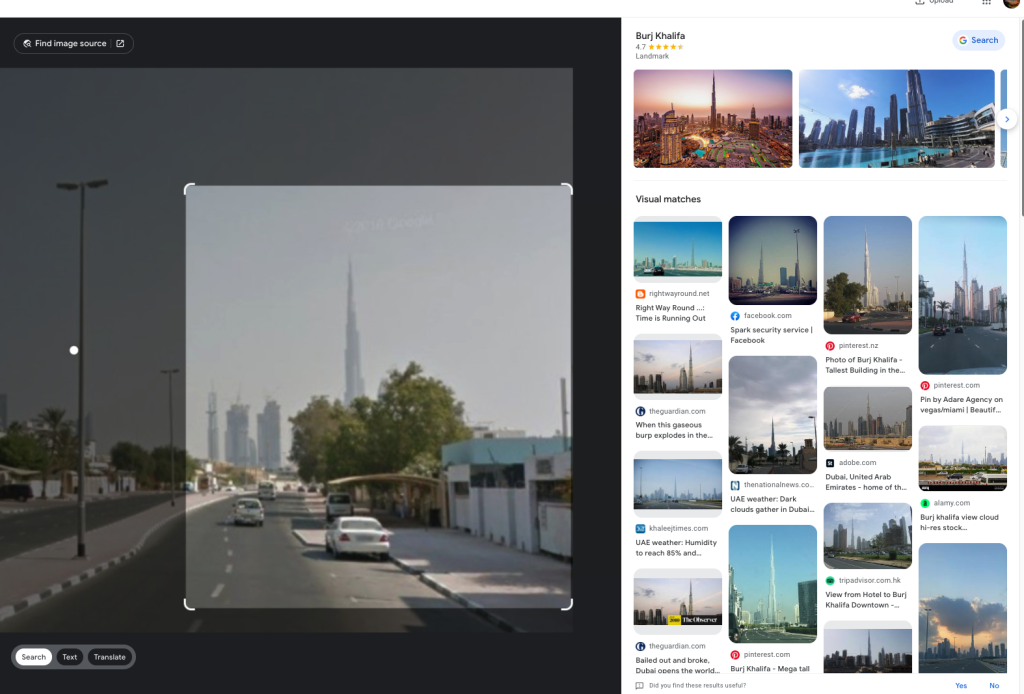
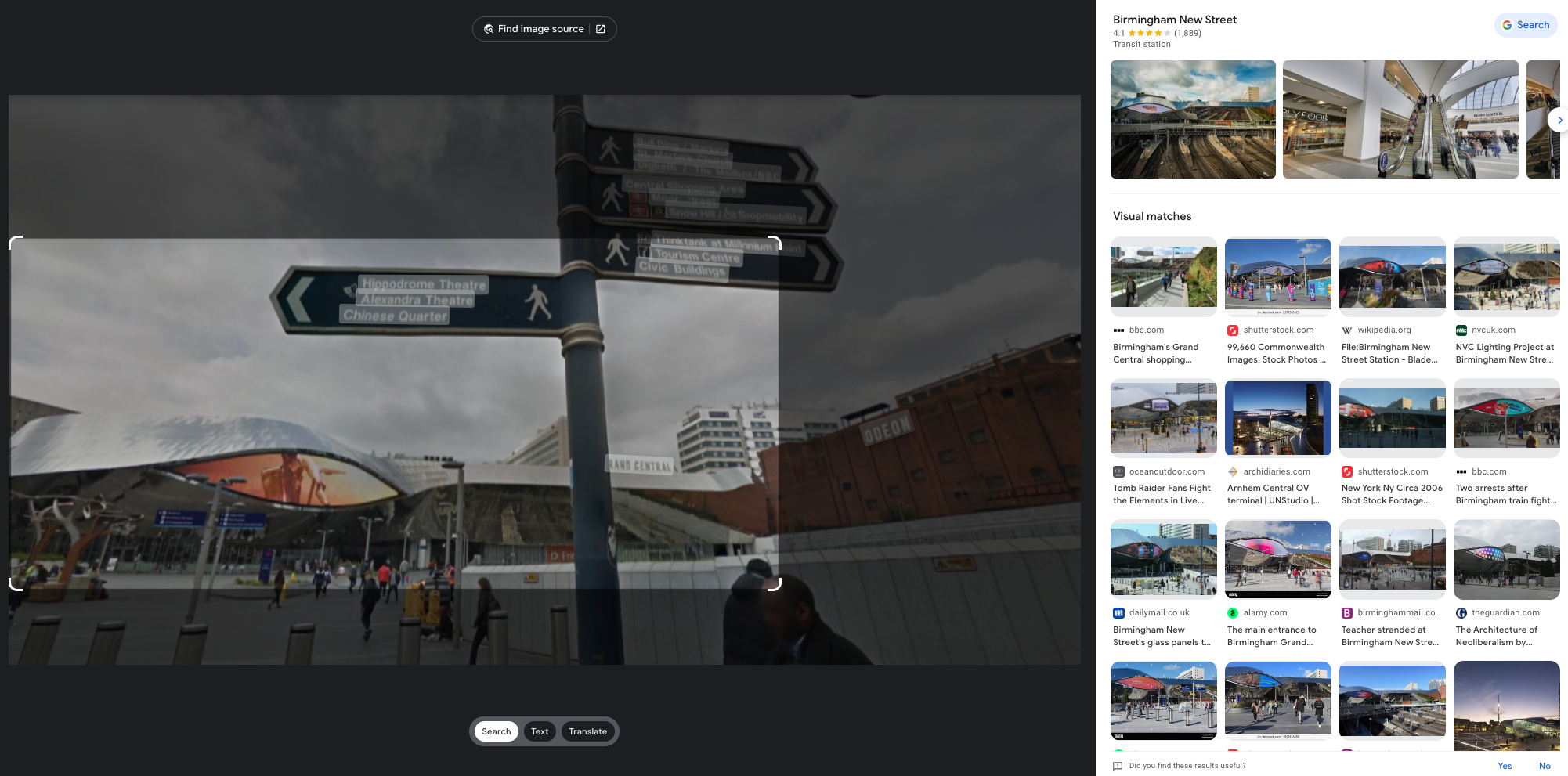
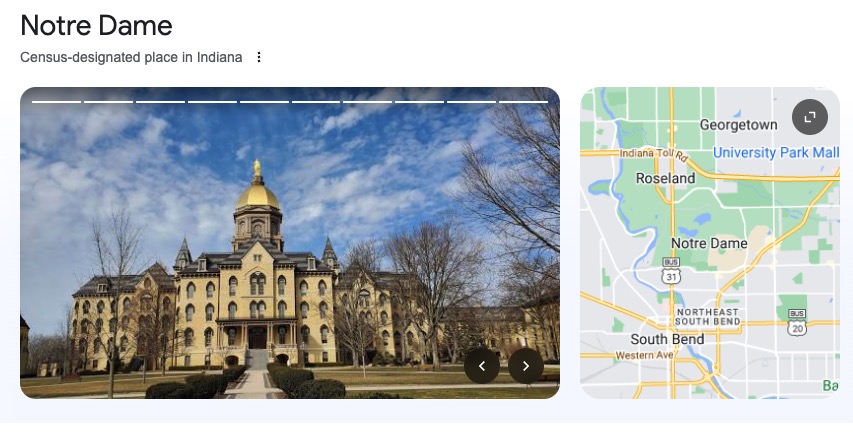
Some of these we have already come across while investigating early information. For the most part this will involve running additional searchs on the information we currently have, such as full name, company, country and even focusing on image searching to see what we can identify. [Question?] Identify their account on a popular business/hiring network? [Question?] Identify their social media account for taking photos? Another google search using only the known alias gives us immediate results to solve this question. [Question?] Identify their community profile for playing PC games and what university club were they in? We can stick with Google to continue our search, or we can try something different. We can also search a number of online platforms by username using something like https://blackbird-osint.herokuapp.com/ [Question?] Where did she go on holiday? Looking at Emilies Instagram account, we can see a photo with a comment from Emily that says “Once in a lifetime holiday here, love me some slings x”. I’m not familiar with the building below, but as soon as she said “slings” I think of the alcoholic drink, Singapore Slings.. lets see [Question?] Which city does she live in? We have some initial clues from the start of this challenge which showed her location on Linkedin as Île-de-France, France, but lets try to confirm this. Reviewing Emilies Instagram account she has posted a picture of a location with the comment “Love working in this beautiful city x”. So lets see if we can confirm where this may be from the photo below. [Question?] Where is her family based (country)? Again, referring back to Emilies’ Instagram profile, we can see two photos that are referred to as being with friends and family. Since we’re not trying to find the exact address, but only the country of residence, we can obtain this quite easily. So we have have been provided with the following image of a building in which the company Emilies works for has an office. [Question?] Which city is the company located? We have a few areas of interest that can aide with our research. We have a unique street sign with a number of landmarks listed in English, we have a very distinct silver building in the background, which for the purpose of this CTF i’ll assume is the building of interest. There’s a large pedestrian only area and in the background we see signs for “Grand Central” which is maybe a transport hub of some sorts. And we also have a brick looking building with “ODEON” on it, which could be a cinema or similar. So lets start with an easy method and reverse image search to see what comes up. Emilie has been observed leaving her apartment and going to the airport. From there she has boarded a flight to another country, but where? our intelligence team has spotted Emilie through a remote IP camera and provided us with the following image. Can we identify which state and country the camera (and Emilie) is in? [Question?] Which state and country is this camera in? We have a couple of things we can focus on in the image. First we have the distinct park layout and the unique architecture. But more importantly we can see that the image has been taken by something called EarthCam and possibly that camera is labeled as “A View from the Dome”. All excellent information points to work on. EarthCam is a webcam Network of live streaming webcams for tourism and entertainment. Searching for the term “Dome” on their website returns 15 camera which at first glance don’t match our image. However the images from the cameras based in Germany have very similar architecture and could be worth a further look. So, my first issue is timing. As I try to check any of these cameras i’m presented with pure darkness as the current time in Europe is around 1:00AM. So rather than view live webcams, I’m now going to search Google Images for static webcam photos. Using the term “earthcam germany dome“. I get a number of results back, but I see two that catch my eye immediately. It’s worth noting, and always good practice to try various search terms. In this case I would have got better results by searching for webcam “a view from the dome”. Time for a slice of accomplishment. Until next time. Task 3
Can you find Emilies other accounts online?
Task 4
Using Emilies social media, find out the following..

Task 5
Find the location of Emilies company.

Task 6
Emilie has left the country, but where is she now?

KaffeeSec - SoMeSINT
Hello again! After having such a great time on Kase Scenarios’ Dark Waters, I’m going to move over to Try Hack Me and attempt some of their OSINT specific challenges – https://tryhackme.com/room/somesint It’s worth noting that this challenge is a number of years old now. And as we know in [...]
| Play | Cover | Release Label |
Track Title Track Authors |
|---|